According to a study by SlashNext, billions of links, attachments, and natural language messages were analyzed over six months in 2022, yielding 255 million attacks – a 61% increase over 2021.
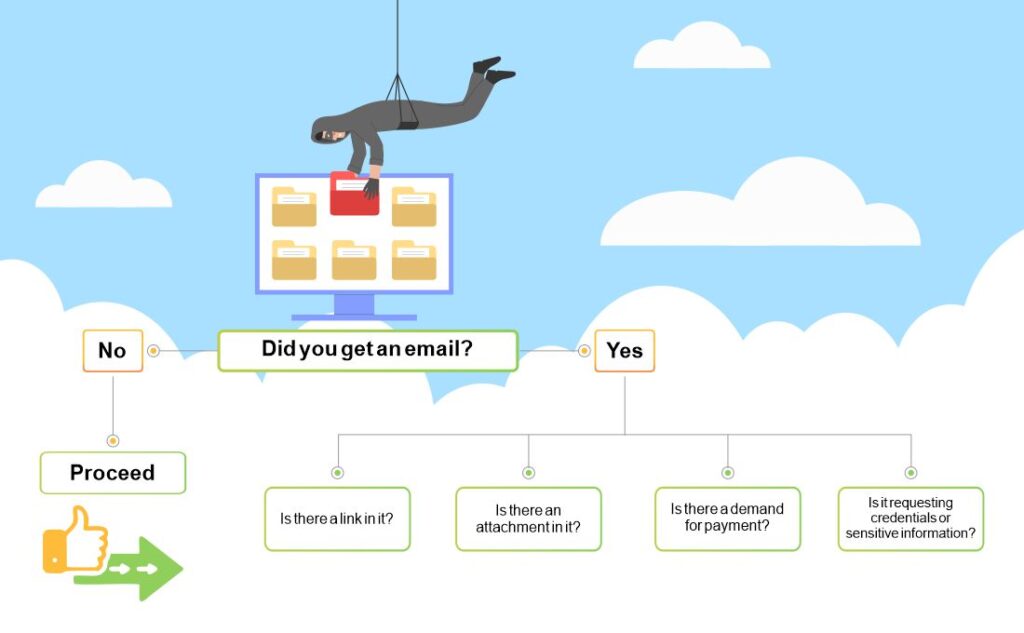
Phishing is a social engineering attack that tricks users into disclosing sensitive information such as logins, passwords, and other personal details. It may seem like you can’t spot a phishing email in the 21st century. But new variants of phishing attacks keep on coming. In fact, their frequency and sophistication continue to increase every year. Fortunately, there are ways to avoid falling victim to phishing scams. These tips will help you identify common phishing scams and recognize when an email is trying to trick you into providing your personal information or clicking on links you shouldn’t trust. With just a little bit of knowledge about how these attacks work and what indicators to look for, you can keep yourself safe from phishing scams.
Is Phishing a SCAM?
In phishing, an attacker sends a fraudulent message to trick the victim into divulging sensitive information, or to deploy malicious software such as ransomware on their infrastructure. The message may be spoofed, fake, or otherwise deceptive. A recent FBI report found that phishing was by far and away the most common attacking method used by cybercriminals in 2020. The number and sophistication of phishing emails keeps growing. Although it may seem impossible to spot a phishing email in the 21st century, new variants keep emerging.
Business Text Compromise, Man in the Middle Attacks, Business Email Compromise, Supply Chain Attacks, Rogue & Malicious Apps & Extensions, Spear Phishing, Social Engineering Scams, Smishing and Credential Phishing are some popular phishing attacks.
Here are a few highlights of Phishing Report for 2022
The number of mobile attacks by cybercriminals has increased by 50%, with scams and credential theft topping the list of payloads.
As of 2022, SlashNext detected an 80% increase in threats from trusted services like Microsoft, Amazon Web Services, and Google, with nearly one third (32%) of all threats being hosted on trusted services.
A staggering 54% of all threats detected by SlashNext in 2022 were zero-hour threats, demonstrating hackers’ ability to adapt in real-time to improve their success rates.
There were 76% spear-phishing attacks designed to harvest credentials
Health care services, professional and scientific services, and information technology are the top 3 sectors targeted by hackers.
Fortunately, there are ways to avoid falling victim to phishing scams. These tips will help you identify common phishing scams and recognize when an email is trying to trick you into providing your personal information or clicking on links you shouldn’t trust. With just a little bit of knowledge about how these attacks work and what indicators to look for, you can keep yourself safe from phishing scams.
Best Ways to Avoid Falling Victim to Phishing Scams
1. Understand What Makes a Good Phishing Email
Phishing emails are designed to trick you, so you’ll often spot them only after it’s too late. There are, however, several indicators that you should pay attention to when reading emails, especially those that are asking you to enter your personal information. A legitimate email will almost always come from a website you’re already logged in to. Sometimes, hackers break into an account and send emails from it to try to trick users into clicking on malicious links or giving out sensitive information. A trustworthy website will also usually provide a clear way for you to report suspicious emails if you think something is off. If you receive an email from a website and aren’t sure if it’s legitimate, you should do a quick Google search to see if there are any reports of suspicious activity.
2. Don’t Click on Links in Emails
The majority of phishing emails come with a malicious link that could direct you to a fake website or prompt you to download a harmful computer virus. Even if you think you can correctly identify whether a site is malicious, you shouldn’t trust your own judgement.
Hackers have become so skilled at creating elaborate phishing websites that even the savviest internet users can fall victim to these schemes. If you’re not sure whether a website is legitimate, type the URL directly into your browser to see what pops up. Bookmark the website’s real homepage so you can visit it directly in the future. If you ever receive an email with a suspicious link, don’t click on it. Even if the link seems to go to a legitimate website, it could be hosting malware.
In that case report the sender’s email address to your internet service provider (ISP) to get their account shut down.
3. Google Is Your Friend
If you suspect you’ve received a phishing email, don’t take the sender’s word for it. Google the terms in the email and see if you get a different result. If you’re not sure how the sender’s information is supposed to look, you could also Google the name of the company along with “phone number” or “website” to see if you get any results.
If something still seems off, you shouldn’t trust the information the sender gave you. For example, if you’re supposed to be receiving a payment from your bank, but the sender’s phone number leads to a completely different company, you may be dealing with a phishing scam.
4. Watch Out for Suspicious Vocabulary
Phishing emails often try to trick you by capitalizing on your emotions. For example, an attacker may use aggressive language or create a sense of urgency to get you to act quickly. You may also see spelling or grammatical errors that would be unusual or unexpected from a legitimate company.
Be especially wary of emails that ask you to provide sensitive information, such as passwords or credit card numbers. If you’re not sure whether an email is legitimate, you can always call the company directly to confirm. And if something about an email seems off, don’t hesitate to do a little digging to confirm you’re dealing with a legitimate company before responding.
5. Be Careful of “Urgent” Requests
Unfortunately, there are also scammers who try to impersonate government officials. For example, you may receive emails claiming that you’ve been caught downloading illegal content or that you owe taxes. Often, these emails will claim that you’re facing dire consequences if you don’t take immediate action.
Urgent requests from government officials will almost always come in the form of a mailed letter that includes contact information. The representative won’t pressure you to take action immediately.
If you receive a phone call from someone claiming to be a government official, you can always hang up and call the government agency yourself to confirm they are actually trying to reach you.
6. Anti-Phishing Toolbar
Anti-phishing toolbars can be added to the majority of widely used web browsers. These toolbars quickly scan the websites you are visiting and contrast them with databases of well-known phishing sites. The toolbar will warn you if you land on a suspicious site. This additional measure of defence against phishing frauds is absolutely free.
7. Update Your Browser Regularly
Security updates for popular browsers are constantly updated. They are made public in response to the security flaws that phishers and other hackers inevitably find and take advantage of. If you disregard notification then, stop ignoring alerts about updating your browsers. Download and install any updates as soon as they become available.
8. Install Antivirus
Antivirus software has special signatures that protect against known technical workarounds and loopholes. Due to the constant invention of new schemes, new versions are continually being added. In order to stop phishing assaults, users should frequently update their anti-spyware and firewall settings. Firewall protection prevents harmful files from being accessed by blocking attacks. Antivirus software scans every file downloaded from the Internet onto your computer.In the event of any suspicion, it will alert you.
9. Deploy Firewalls
An effective firewall serves as a barrier between you, your computer, and outside intruders. You should deploy two types of firewalls: a desktop firewall and a network firewall. The first option is a software kind, and the second is a hardware type. Together, they significantly lower the chances that hackers and phishers will get access to your computer or network.
Stay Vigilant and Learn to Recognize Scams
Above all, you have to remain vigilant and be careful not to fall for phishing scams. If you’re not sure about an email, call the company directly and confirm the message is real.
You may also report a suspicious email to your ISP or create a phishing report to help others avoid falling victim to the same attack. Ultimately, phishing scams are successful because people are tricked into falling for them.
However, following these tips, you can avoid falling victim to phishing scams. With a little bit of awareness and attention to detail, you can protect your personal information and avoid being tricked by a hacker’s malicious emails.
Keep Calm, NS3TechSolutions’ Eagles will Keep Your Business Running
Cyber threats affect 85% of organizations that go digital without taking adequate precautions. NS3TechSolutions vigilant SOC Team is here to help your business on going. Our services for businesses include email security, threat intelligence, ongoing detection, prevention, and response. We work as a team to manage events, report on incidents, and send alerts that can be taken in response to vulnerable incidents. Our security professionals integrate industry-leading SIEMs and automated response capabilities to meet security and compliance goals, reduce the risk of data breaches, and save money on operational costs.
For more information-
Visit Our Website 🌐 : www.ns3techsolutions.com
For Queries-
Call us 📞 +91-981 055 7611
Email us 📨 [email protected]

